How to Encrypt Files, Folders and Drives on Windows
One of the best means to protect your privacy is to encrypt important information on your computer. Whether you need to send personal information to someone, or simply want to brand certain that no one who gets access to your figurer can come across stuff you would rather go on individual, encryption is the style to go.
Editor's Note:
Guest writer Heinrich Long is a writer at Restore Privacy, a weblog dedicated to inform about best online privacy practices, secure your electronic devices, unblock restricted content and defeat censorship.
As a Windows x user, you have numerous options for encrypting information. In this guide we will bear witness yous means to encrypt individual files, file folders, and fifty-fifty entire disk drives. Each approach has its own benefits and drawbacks, so we'll cover those, too. That way, you'll take a better sense of which type of encryption yous volition need for diverse situations. Before nosotros get farther, here are a couple of points to keep in listen:
- With Windows 7 at present unsupported, and Windows 8 all-time forgotten as fast as possible, this guide deals only with the Windows x operating system.
- If you lot are encrypting a file to share with someone else and need to give them the password, you should not send them that password using the same method that you send them the file. For case, if yous plan to email them the file, it would be a big security run a risk to also electronic mail them the countersign. Ideally give them the password over the telephone, a secure messaging app like Signal or Wickr Me. At the very to the lowest degree transport it via a unlike electronic mail service than the i you will use for the file.
Now let'south talk almost when to use the 3 types of encryption that yous tin can use:
- Individual file encryption
- Folder encryption
- Hard bulldoze / Disk encryption
Individual file encryption
As the name implies, individual file encryption refers to encrypting one file at a fourth dimension. Each file has its own password or key.
Individual file encryption is great for files you plan to share or store in the cloud. Windows 10 users can encrypt individual files using a tool like vii-nada. You can also encrypt individual Microsoft Office files from within their apps, although this is better suited to casual person apply than protection against serious adversaries.
Folder encryption
Next up is folder level encryption. This approach involves encrypting everything that is stored in a folder. Passwords or keys are assigned to the binder, non individual files.
Folder encryption is a great organizational tool. For case, you could create a different encrypted folder for each fellow member of your family. Give Emerge only the countersign for her binder, and Jimmy only the countersign for his, and each can have their ain private space on the same device.
Note that storing a file in an encrypted folder doesn't prevent you from as well encrypting files individually.
Hard drive / Disk encryption
Hard drive or deejay encryption protects the entire drive at once. To use a device with an encrypted difficult drive you lot would demand to enter the countersign or key when you logged on, or nothing on the disk would be accessible.
This kind of encryption is a good beginning line of defense force in case of theft. If someone stole your laptop, or ripped the drives out of one of your servers, they would demand to defeat the hard drive encryption to get any data at all.
Yous tin still apply binder level encryption and private file encryption to an encrypted deejay.
Password management and file encryption
Before nosotros swoop into the details of file encryption, we need to make an important note on passwords. You demand to be using a skillful countersign manager, forth with good password hygiene.
Why is that? Well, if you lose or forget the countersign for accessing your encrypted files, then they'll probably be gone for skillful. A good countersign manager is disquisitional. Nosotros've reviewed many options, including 1Password, LastPass, and many more.
See our guide on the best countersign managers for the top recommendations and step-by-step data for good countersign management. Now that we've hit the basics, information technology is fourth dimension for some specifics. Let's start with…
How to encrypt files and folders on Windows x
Your options for encrypting files and folders on Windows ten devices depend on which version of Windows 10 you have. Windows 10 Pro and Enterprise users have a built-in encryption tool chosen the Encrypting File Arrangement (EFS). Any Windows 10 user, including those with the Home edition, can also utilize third-party apps such equally 7-aught for file and folder encryption.
Beyond these options, Microsoft Function apps accept a bones file locking / encryption feature built in, as does Adobe Acrobat. Nosotros'll round out our coverage of Windows 10 encryption by taking a look at these.
How to encrypt files and folders with the Encrypting File Organisation (EFS)
The Encrypting File System (EFS) is built into the Professional and Enterprise versions of Windows 10. Information technology is treated as an Advanced characteristic of the Windows File Explorer. This makes a lot of sense, since used carelessly, EFS can go out yous with files you lot tin can never admission again.
EFS does all its encryption work in the background, including automatically creating a File Encryption Cardinal (FEK), and encrypting that key then only the business relationship that encrypted the file tin decrypt it. All this happens automatically and transparently.
Aside from a lock symbol that appears in the File Explorer next to a file or folder that is encrypted, there is no piece of cake way to tell that a file or folder is encrypted with EFS.
Unfortunately, EFS has some quirks that make information technology a less than ideal choice for many uses. Knowing what these are will help yous determine whether EFS is the reply to your Windows 10 file encryption needs:
- EFS only works on drives formatted with NTFS.
- If you move an EFS-encrypted file to a disk formatted with FAT32 or exFAT, it becomes decrypted.
- If you movement an EFS-encrypted file across a network, or send it with an email bulletin, it becomes decrypted.
If these quirks haven't scared you away, here's how to encrypt files and folders with EFS:
- Launch Windows File Explorer and navigate to the file or binder you want to encrypt using EFS.
- Right-click the file or folder you lot want to encrypt.
- In the card that appears, select Properties.
- In the General tab of Backdrop, detect and click the Advanced push (it is circled in red in the following image).

- In the Avant-garde Attributes dialog box that appears, set the Encrypt contents to secure data checkbox.
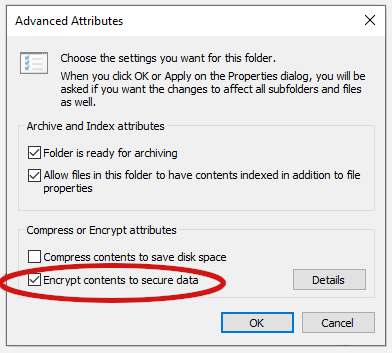
- Click OK until you return to the document window.
That is all you demand to do, from now on, the encrypted file or binder will appear encrypted to anyone other than the user account that encrypted the particular in the first place.
How to encrypt files and folders with 7-zip
seven-zip is a freeware file compression program that can besides encrypt files and folders using AES-256 encryption, which is the manufacture standard for nearly encrypted systems. If you programme to use 7-zip to encrypt files or folders yous should know that the process creates an encrypted copy of the file or folder. The original, unencrypted file or folder is unchanged.
If you are creating the encrypted item because you plan to send it somewhere, or store it in the cloud or something similar that, this is fine. But if your goal is to protect the files and folders on your own device, this isn't ideal.
In the balance of this department, we'll beginning look at how to encrypt files and folders with 7-zip. After that we'll talk virtually what else you demand to practise if your goal is to protect the files and folders on your own device. The following instructions assume you already accept 7-goose egg installed on your arrangement. If not, you can download it here.
How to encrypt Windows 10 files and folders using vii-aught
- Correct-click the file or folder you lot want to encrypt.
- In the shortcut carte that appears, select 7-Cipher, and then Add together to annal…. This opens the Add to Annal window.

- In the Archive field, enter the name for the archive you lot will create.
- In the Annal format list, select zippo.
- In the Encryption section of the window, enter a stiff password in the Enter password field, and again in the Reenter password field.
- In the Encryption Method list, select AES-256.
- Select OK. This creates the encrypted archive file, which appears in the same folder as the file or binder yous encrypted.
What to practise subsequently you lot encrypt something with 7-zip
The result of encrypting something with 7-nix the fashion we did here is a zipped annal that is AES-256 encrypted. This archive appears in the same folder as the file or folder that you encrypted, alongside the original file or folder. What this means to y'all depends on what you plan to do with the encrypted file or folder.
If you created the archive to share copies of the file or binder, this is fine. Just send the archive to the recipient. Assuming they have 7-zip or a similar plan on their arrangement (and you securely conveyed the password to them somehow), they will be able to unzip the archive, and then double-click the file to enter the password in a dialog box like this 1:

Once they do that, the operating system should open the file in whatever app is appropriate, and the recipient tin view it, or save it, or practise any is necessary with information technology. Annotation that they volition still have the encrypted files on their system every bit well.
If y'all created the archive to protect the files or folders on your system, you lot should skip downward to the section titled, "Eliminate any possible unencrypted copies of the file" once you are done encrypting files and follow the instructions at that place to make sure no unencrypted copies of things are lying around where some snoop tin find them.
How to encrypt Microsoft Part files on Windows 10
Some applications now accept options to encrypt the types of files they themselves apply. For example, Microsoft Give-and-take tin can encrypt Word files, and Adobe Acrobat can encrypt PDF files. We'll demonstrate this below.
How to encrypt files using Microsoft Part on Windows
Allow's use Microsoft Give-and-take to show how information technology is washed by encrypting a simple Discussion document.
- With the document y'all desire to encrypt open in Give-and-take, select File, then Info.
- In the Info window, select Protect Certificate.
- In the carte du jour that appears, select Encrypt with Password.

- In the dialog box that appears, enter the password you want to use for this certificate.

From at present on, the only style to view this document will be by entering the password when prompted from inside a Microsoft Role application that supports the unencrypted file type. But please see the next department to eliminate any possible unencrypted copies of the file on your estimator.
Eliminate any possible unencrypted copies of the file
If you use 7-zip or Microsoft Office to encrypt files, it is likely that Windows 10 still has ane or more temporary copies of the unencrypted files stashed on the disk. To exist safe, y'all will want to delete all temporary files one time you are done encrypting things.
How to delete any possible unencrypted copies of the file
- Click Start, and then blazon temporary into the search box. In the carte that appears, select Delete temporary files. This opens the Storage settings window.
- Windows 10 scans your arrangement and displays a list of file types that are stored on the diverse deejay drives of your system. Select Temporary files to encounter a listing of the file types that are available to delete.
- In that list, set up the Temporary files and Recycle Bin checkboxes, and so click the Remove Files button at the top of the listing to obliterate any unencrypted copies of the file that might withal be floating effectually on your system.
How to encrypt difficult drives on Windows 10
When it comes to disk encryption on Windows x, BitLocker Device Encryption is the tool that Microsoft provides. Built into Windows ten Pro and Enterprise, BitLocker Device Encryption does exactly what information technology sounds like – it encrypts all the storage devices in your arrangement.
This sounds platonic, but there are some drawbacks to using BitLocker.
- If BitLocker Device Encryption wasn't preinstalled and configured on your figurer, it can be a real headache to install and configure. Check out this Overview of BitLocker Device Encryption posted on Microsoft.com.
- BitLocker has unlike capabilities depending on what hardware your computer has built onto its motherboard.
- As mentioned earlier, BitLocker only works on Windows 10 Professional and Enterprise systems.
Happily for us, there is a great culling available. Called VeraCrypt, it addresses all of the drawbacks nosotros just saw:
- VeraCrypt is significantly easier to install than BitLocker.
- VeraCrypt is not dependent on special hardware congenital into your computer.
- VeraCrypt works on every version of Windows 10, not merely Pro and Enterprise.
VeraCrypt is Costless, Open Source Software (FOSS), which we really like. Without getting into the OpenSource vs Proprietary software argument that plagues the figurer world, from our perspective, FOSS software is by and large considered more secure, and of course is costless to use. One time VeraCrypt is installed, all y'all need to do is enter your VeraCrypt password whenever you get-go the calculator.
Given all that, you lot know where we're going with this. In the following section nosotros'll walk you through installing VeraCrypt on one of our lab machines. Ready?
How to install VeraCrypt for Windows 10 hard drive / deejay encryption
While installing VeraCrypt is much simpler than the alternative, in that location is more to it than just launching an installer and pressing Okay a few times. And if you lot mess upwards, there is a chance y'all will lose files or even access to the entire disk bulldoze.
We advise you read through the instructions that follow before starting the process. If y'all are not confident you tin can complete the steps shown, or if y'all accept a bad habit of losing important passwords, information technology is meliorate to skip this blazon of encryption.
Installing VeraCrypt
Here are the steps to install VeraCrypt on Windows 10:
- You will need a standard USB drive for the VeraCrypt Rescue Disk you will create later on. Find yourself a USB drive you can dedicate to this, and format it every bit Fatty or FAT32 and so it is ready when we need it.
- You will also need a program that tin can unzip files. We recommend 7-nil, the free and open source nil program we have discussed elsewhere in this guide. You can download 7-zip here.
- Go to the VeraCrypt download page and await for the Windows Installer.
- Launch the VeraCrypt setup plan and accept all the default options displayed in the Setup Wizard.
- Afterward a moment, VeraCrypt should display a message stating that "VeraCrypt has been successfully installed."
- Click OK to close the Wizard, and then Finish to complete the installation process. VeraCrypt will display the message shown below.

- If you are new to VeraCrypt, it is worthwhile to follow the advice given here and view the tutorial. Click Yep to view the tutorial, or No to skip it. Either way you lot get is fine since we will walk y'all through the remainder of the steps right here.
- Launch VeraCrypt. Select the Organisation card, then Encrypt System Partition/Drive.

- The VeraCrypt Volume Creation Wizard appears. The Wizard asks what type of system encryption y'all want: normal, or hidden. Normal merely encrypts the system division and is what we want, and so select Normal, then click the Next push to proceed.
- Next the wizard volition ask you lot whether to encrypt only the Windows arrangement partition, or the unabridged drive. If you accept multiple partitions with of import data, you can encrypt the whole drive. If y'all only have one partition on the bulldoze (as we practise on this computer), VeraCrypt will only allow you select the Encrypt the Windows system partition option. Make your choice and click Next when set.

- The Wizard displays the Number of Operating Systems window. Is your organization dual-boot or multi-kick (you tin start the organization in various operating systems)? If so, select Multi-boot. Otherwise, select Single-boot. Click the Adjacent button to proceed.
- The Wizard displays the Encryption Options window. We recommend you lot choose AES for the Encryption Algorithm, and SHA-256 for the Hash Algorithm. Both are widely-used algorithms that will serve you well. Click the Side by side button to continue.
- The Wizard displays the Password window. Information technology is important to choose stiff passwords if you want your organization to exist secure. Many countersign director programs (such as our pinnacle pick, Bitwarden) include password generators that can assistance you create a strong ane. Note: VeraCrypt will hassle yous about it if you choose a password less than xx characters long. Click the Side by side button to keep.
- The Wizard displays the Collecting Random Data window. You will be required to move your mouse around randomly within the window. This additional randomness increases the strength of your encryption keys. In one case the randomness meter at the bottom of the window is total you can click the Next button to go along.
- The Wizard displays the Keys Generated window. There is cipher you need to do hither except click the Next button to keep.
- The Wizard now forces yous to create a VeraCrypt Rescue Disk (VRD). The explanation for this appears in the post-obit image. If you want to live dangerously you can set the Skip Rescue Disk verification checkbox to avoid being forced to create a physical rescue disk. Make note of where VeraCrypt says it will store the ZIP prototype, then click Next to continue.
- Unless you selected the Skip Rescue Disk verification selection in the concluding step yous are now going to be forced to create a physical rescue deejay and permit VeraCrypt to inspect it to meet if you did it right. VeraCrypt doesn't tell you how to practice this or assist in whatever mode, only nosotros can. Recollect finding a spare USB bulldoze a footling while ago? Information technology is time to insert that USB bulldoze into your system. Now navigate to the location where VeraCrypt stored its Rescue Disk in the previous step. Utilise 7-goose egg (or another ZIP plan) to extract the files in the VeraCrypt Rescue Disk.nil file directly to the root of the USB bulldoze. One time that is done, click Side by side and then VeraCrypt can check your work.
- Assuming all went well, you should now see the Wizard'south Rescue Disk Verified window. Remove the USB drive from the figurer and click Adjacent.
- The Wizard displays the Wipe Manner window. For any normal uses, you don't need to worry near this. Make sure the Wipe Mode is set to None (fastest) and click Next to continue.
- Nosotros are getting there. The Magician now displays the System Encryption Pretest window. This is where VeraCrypt checks to make certain that the encryption process will actually work, rather than assuming it will work and trashing your system if information technology doesn't. The image below explains what will happen in detail. Click Test to run into how information technology goes. Notation that VeraCrypt will probably ask you to print some more warnings and emergency procedures and the like before information technology really does the test, so be ready for that.
- Assuming everything went well, you should see the following window once you accept successfully restarted your figurer and passed the system encryption pretest.

- VeraCrypt recommends y'all to make fill-in copies of all your important files before y'all encrypt your system. This volition permit you to recover if something desperate like a power failure or system crash occurs in the middle of the encryption procedure. Once you are washed with that, have a deep breath and click Encrypt. VeraCrypt volition display more documentation it wants you to print if possible, covering when to use the VeraCrypt Rescue Disk after the encryption process is consummate, and so will finally brainstorm the actual encryption process. You'll exist able to monitor the progress of the encryption, which is a nice touch.

- Once the encryption is done, y'all will need to enter your VeraCrypt password every fourth dimension you lot showtime the computer.
What We Learned
Encrypting important information is one of the all-time things yous can do to protect yourself from everyone who is trying and then difficult to get their hands on your personal information.
In this guide we covered techniques that Windows 10 users can use to encrypt individual files, folders, and entire drives on their Windows systems. While no one can guarantee that your information will be 100% safe against whatever and all attacks, the simple deed of encrypting your most important data can make a big difference.
Masthead credit: eamesBot
Source: https://www.techspot.com/guides/2069-how-to-encrypt-windows/
Posted by: torresdickclonsund.blogspot.com


0 Response to "How to Encrypt Files, Folders and Drives on Windows"
Post a Comment